Failed to Create Cbs Worker - Waiting for a Second and Trying Again [hresult = 0x800700c1]
The below mail initially stemmed from an Exchange Gamble Assessment which noted that all of the customer's Commutation servers were missing critical Windows updates. The customer's security team were slightly upset every bit they believed (mistakenly) that all assets were properly updated. This was non the instance. When we looked into the details, the monthly Windows Server 2012 R2 updates had been failing to install for the last eighteen months....
Notation that Windows vii and Windows Server 2008 R2 changed their update methodology in October 2016 to mirror the update distribution behaviour in newer versions of Windows.
The Windows Component Store was introduced in Windows XP to back up next assemblies and enhanced in Vista track all the Os components. For those who worked on NT or Windows 2000/2003 servers there are always some funny stories around managing the OS over fourth dimension. For instance if you wanted to install an OS feature on a Windows Server 2003 SP2 automobile, potentially you lot needed to provide RTM, SP1 and SP2 source files. This was due to how the installation .inf files were chained as the OS was updated over fourth dimension with service packs and hotfixes. Windows knew information technology needed particular files from a item source and would prompt every bit needed. Well, non always. Sometimes that went a scrap wrong.
NT had its own quirk where there was no chaining. After installing an Os component you had to reapply the service pack. The act of re-applying the service pack would over write the older file from the CD with the new file from the service pack. Yes, that really was a thing.
Later on having to deal with those issues for 15 years, CBS promised much goodness. Typically though, two things happened to sour an admin on CBS. Firstly they saw the perceived size of the C:\Windows\WinSxS folder, and secondly they experienced CBS corruption.
In may cases, the first indication of a CBS issue was Windows Update failing to install an update. Trying to install the update manually afterwards downloading from the Windows Update Catalog, or using Windows Update would ever fail. In that location are many Windows Update failure codes and each has their ain root cause.
Annotation that you tin straight search for a given update in the Windows Update Itemize, add to basket and and so download it. This can be very useful when trying to right the effect – more on that trick later.
Symptoms
Equally mentioned earlier, there are a range of error codes reported past Windows Update when information technology cannot service the OS. In addition to CBS preventing updates from installing, I've too seen other "interesting" issues such as:
-
Substitution DAG fails to install as the underlying OS cluster components tin not install
-
SCOM agent crashing on NTdll.dll exception
-
Commutation IIS app pools crashing on process exceptions
-
Out of retentivity and assorted performance issues
The archetype WindowsUpdate.log or the new Become-WindowsUpdateLog cmdlet will log the failure from a Windows Update perspective. All the same if the underlying issue is due to CBS and so we need to look at logs which are focused on that area. The best examples of such logs are the DISM and CBS logs which can exist found in the corresponding locations below:
- C:\Windows\Logs\DISM\DISM.log
- C:\Windows\Logs\CBS\CBS.log
Typically the DISM log will state that there is a CBS issue, and we demand to expect into the CBS.log to identify the particular bundle which has the effect.
The below example shows Windows Update failing with error lawmaking 0x800f0831.
2018-01-28 13:14:06, Info CBS Store corruption, manifest missing for bundle: Package_56_for_KB3081320~31bf3856ad364e35~amd64~~6.3.i.one
2018-01-28 thirteen:14:06, Error CBS Failed to resolve package 'Package_56_for_KB3081320~31bf3856ad364e35~amd64~~6.3.1.1' [HRESULT = 0x800f0831 - CBS_E_STORE_CORRUPTION]
2018-01-28 13:14:06, Info CBS Mark store corruption flag because of package: Package_56_for_KB3081320~31bf3856ad364e35~amd64~~six.3.1.ane. [HRESULT = 0x800f0831 - CBS_E_STORE_CORRUPTION]
2018-01-28 thirteen:xiv:06, Info CBS Failed to resolve packet [HRESULT = 0x800f0831 - CBS_E_STORE_CORRUPTION]
2018-01-28 13:14:06, Info CBS Failed to go next package to re-evaluate [HRESULT = 0x800f0831 - CBS_E_STORE_CORRUPTION]
2018-01-28 13:14:06, Info CBS Failed to process component watch listing. [HRESULT = 0x800f0831 - CBS_E_STORE_CORRUPTION]
Remediation Tools
Depending upon the exact effect, you may need to run one or more of these tools:
-
CHKDSK
-
DISM
-
SFC
If yous piece of work for Contoso, the elementary commands listed in the get-go section will suffice. In reality though, things can get quite squirrely and we need to look at more avant-garde and/or different options.
That is covered in the latter department of this post.
CHKDSK
CHKDSK.exe tin bank check and correct a volume'due south file system. This may be required if the NTFS filesystem is doubtable afterward a storage "event".
The CHKDSK tool is documented hither.
The below is an instance for scanning a local motorcar's C:\ drive.
CHKDSK.exe C: /R /F /B
This volition crave a reboot and considerable time to then perform the browse. There are other options to perform SpotFix and online scans in newer versions of Windows, though that may not help that much for the OS drive depending on the issue.
DISM Browse
Annotation that Deployment Image Servicing and Management (DISM) can exercise multiple tasks on the Windows Bone. Here we will focus on the scanning and repairing of CBS issues. DISM is non bachelor for Windows Server 2008 R2 for example and the System Update Readiness (SUR) tool should be used.
At that place are a some different options that tin can exist used:
-
DISM.exe /CheckHealth
-
DISM.exe /ScanHealth
-
DISM.exe /RestoreHealth
Use /CheckHealth to check whether the image has been flagged as corrupted by a failed process and whether the corruption can be repaired.
Use /ScanHealth to scan the image for component shop corruption.
Employ /RestoreHealth to scan the image for component store abuse, and then perform repair operations automatically.
Use /Source with /RestoreHealth to specify the location of known good versions of files that can be used for the repair. For more than information on specifying a source location, see https://become.microsoft.com/fwlink/?LinkId=243077.
Apply /LimitAccess to prevent DISM from contacting WU/WSUS
Note that the /Online specifies nosotros will work with the electric current Windows installation rather than correct an offline image using the /Image switch.
Example: DISM.exe /Image:C:\offline /Cleanup-Image /RestoreHealth /Source:C:\Exam\Mountain
Most of the online articles will specify to start with this command to scan and repair CBS:
DISM.exe /Online /Cleanup-Image /RestoreHealth
We will come back to DISM later, with some more advanced options.
SFC
Once DISM has done its work, time to run SFC.
SFC.exe is the Organisation File Checker utility which will browse and verify the integrity of protected system files. Should an incorrect version be plant, information technology can be replaced.
The SFC tool is documented here.
Example syntax to scan and repair the local machine would be:
SFC.exe /SCANNOW
Typically this is run AFTER DISM reports no issues.
IF Squirrel Gene > 10
If the standard DISM commands exercise not right the result, and so its time to break out the rough stuff. In many cases a DISM /RestoreHealth ends in an error stating that the source files could not be constitute. By default DISM will typically endeavour to contact Windows Update to download the required components. If the default location for Features on Demand is specified then that location is used.
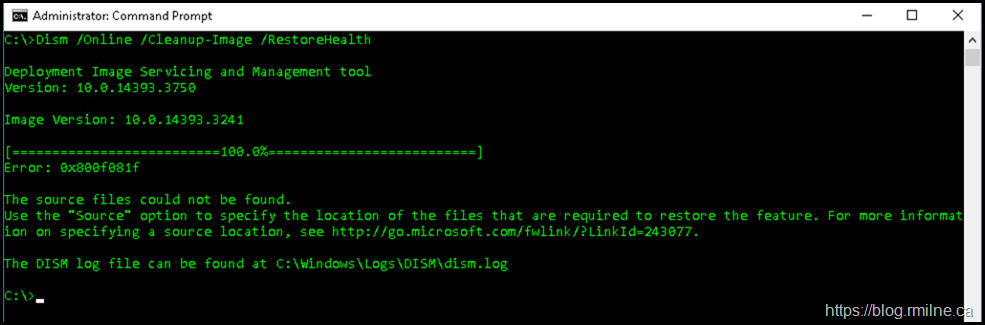
The error text is included for accessibility.
C:\>Dism /Online /Cleanup-Epitome /RestoreHealth
Deployment Image Servicing and Management tool
Version: 10.0.14393.3750
Epitome Version: 10.0.14393.3241
[==========================100.0%==========================]
Error: 0x800f081f
The source files could non be found.
Use the "Source" option to specify the location of the files that are required to restore the feature. For more information on specifying a source location, see http://go.microsoft.com/fwlink/?LinkId=243077.
The DISM log file tin can be found at C:\Windows\Logs\DISM\dism.log
Note: There are some known bug with the PowerShell components so you lot may want to review this commodity.
Then we need to signal DISM at a location where the relevant files are available. Even so in order to determine a suitable location, we need to identify which component is causing the issue.
Is information technology a base function of the OS or an update that was installed? If it is a base of operations OS component and then nosotros could utilise the install WIM located on the install media. If the required component is an update that was downloaded and installed, i.e. non office of base DVD image, and then we need to access a WIM that has that component installed. Alternatively a separate server which has the update in question installed can be used.
How to decide which component is causing the issue?
If nosotros open up up the the C:\Windows\Logs\DISM\DISM.log in Notepad, nosotros can run into the fault 0x800f081f listed there:
2020-08-06 13:35:52, Info DISM DISM Bundle Manager: PID=6472 TID=6784 Error in operation: source for packet or file non found, ResolveSource() unsuccessful. (CBS HRESULT=0x800f081f) - CCbsConUIHandler::Error
2020-08-06 13:35:52, Error DISM DISM Package Manager: PID=6472 TID=13972 Failed finalizing changes. - CDISMPackageManager::Internal_Finalize(hr:0x800f081f)
Still, what component is actually failing? let's look in the CBS.log for those details. In the CBS.log nosotros run into:
p) CSI Payload Decadent amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpThreatCatalog.cdxml
Repair failed: Corrupted replacement payload.
In the instance above it is an OS PowerShell component which is experiencing an issue. Information technology it were an update, then you would see the relevant KB number listed.
In order to fix this we need to specify where DISM can become the required files. That may prove to be catchy as not all of the syntax for all options are fully laid out.
We accept a few different options to get the required files:
-
Contact Windows Update
-
A different Windows install which contains the required files
-
Mountain a WIM prototype file to the local file system.
-
Access a WIM image file directly
Risk are that the WU pick already failed, else you would not exist reading this far down the page. If we desire to look at a WIM file to list the images inside, to ensure we take the correct source the below command will assistance:
DISM.exe /Become-ImageInfo /ImageFile:Install.wim
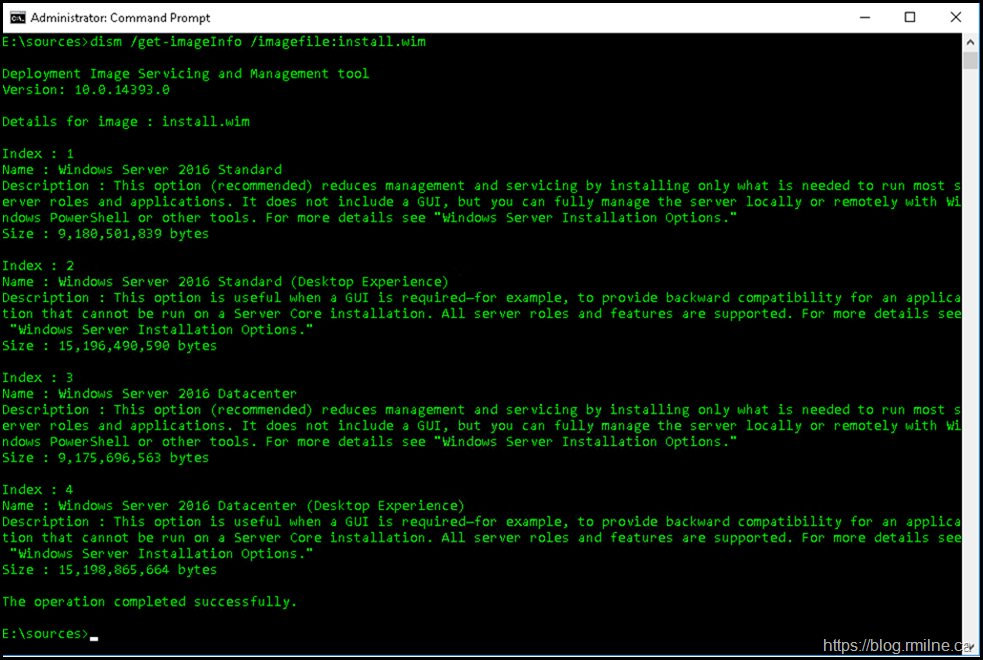
Nosotros volition use the 2nd image as it is a friction match. We specify that at present in the DISM command – note the :2 syntax after the WIM file proper name.
DISM /Online /Cleanup-Image /RestoreHealth /Source:wim:E:\Sources\Install.wim:2 /LimitAccess
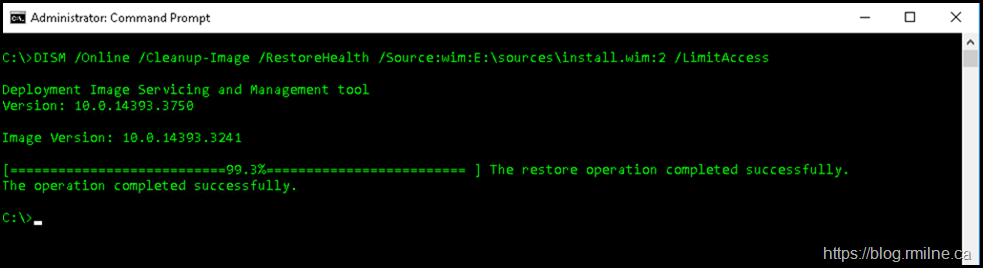
In the CBS.log file
Checking System Update Readiness.
(p) CSI Payload Decadent (Fixed) amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpThreatCatalog.cdxml
(p) CSI Payload Decadent (Fixed) amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\Defender.psd1
(p) CSI Payload Corrupt (Fixed) amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpWDOScan.cdxml
(p) CSI Payload Decadent (Fixed) amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpSignature.cdxml
(p) CSI Payload Decadent (Stock-still) amd64_windows-defender-direction-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpThreat.cdxml
(p) CSI Payload Corrupt (Stock-still) amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpComputerStatus.cdxml
(p) CSI Payload Corrupt (Fixed) amd64_windows-defender-direction-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpScan.cdxml
(p) CSI Payload Corrupt (Fixed) amd64_windows-defender-management-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpThreatDetection.cdxml
(p) CSI Payload Corrupt (Stock-still) amd64_windows-defender-direction-powershell_31bf3856ad364e35_10.0.14393.0_none_1137c685b804c9a3\MSFT_MpPreference.cdxml
Summary:
Functioning: Notice and Repair
Operation result: 0x0
Running another /RestoreHealth browse shows that CBS is at present healthy.
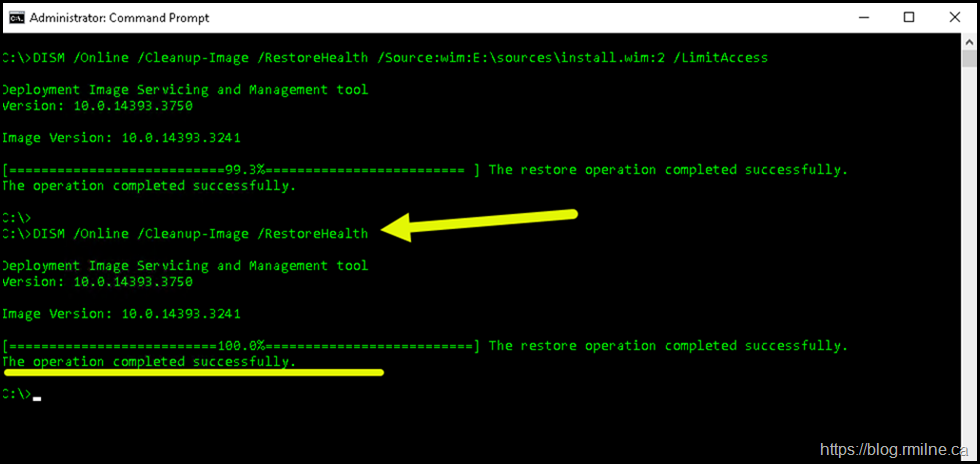
Then we run SFC to validate system files. Note that corrupt files were found and replaced.
For reference, below are the entries from the CBS log showing the activity.
2020-08-06 21:42:14, Info CSI 00007d39 Hashes for file fellow member \??\C:\Windows\System32\WindowsPowerShell\v1.0\Modules\Defender\MSFT_MpPreference.cdxml do not match actual file [l:23]'MSFT_MpPreference.cdxml' :
Plant: {l:32 3VV5hrUQdPPkt9XAkjkDvxC6kZoSNWBfXLqKSbBe8H0=} Expected: {50:32 zbiTyZoXoGxGmd+AOLbOJqmYHoTwkMkcKkoXw+Uz/ng=}
2020-08-06 21:42:xiv, Info CSI 00007d3a [SR] Repairing corrupted file \??\C:\Windows\System32\WindowsPowerShell\v1.0\Modules\Defender\MSFT_MpPreference.cdxml from shop
2020-08-06 21:42:xiv, Info CSI 00007d3b@2020/8/7:01:42:fourteen.130 CSIPERF - FileMapsCreated 113ms
2020-08-06 21:42:14, Info CSI 00007d3c CSIPERF - FilePI Commit 116ms
2020-08-06 21:42:14, Info CSI 00007d3d@2020/viii/7:01:42:14.146 Archaic installers committed for repair
2020-08-06 21:42:14, Info CSI 00007d3e [SR] Repair complete
2020-08-06 21:42:14, Info CSI 00007d3f [SR] Committing transaction
2020-08-06 21:42:14, Info CSI 00007d40 Creating NT transaction (seq 1), objectname '(null)'
2020-08-06 21:42:14, Info CSI 00007d41 Created NT transaction (seq one) result 0x00000000, handle @0x3fc
2020-08-06 21:42:14, Info CSI 00007d42@2020/viii/7:01:42:14.257 Offset NT transaction commit...
2020-08-06 21:42:fourteen, Info CSI 00007d43@2020/eight/vii:01:42:14.278 CSI perf trace:
CSIPERF:TXCOMMIT;21310
2020-08-06 21:42:14, Info CSI 00007d44 [SR] Verify and Repair Transaction completed. All files and registry keys listed in this transaction take been successfully repaired
DISM - Remote Server
If another motorcar has the required components, then we can point to that. The beneath uses a server called Exch-2016 and hits the admin $ share to obtain the files from that other motorcar's WinSXS folder.
DISM /Online /Cleanup-Image /RestoreHealth /Source:\\Exch-2016\c$\Windows\winsxs /LimitAccess
Annotation - ensure that you have admission to the required resources from the cmd prompt where you lot are running this. If in doubt, map a drive to provide the credentials and use the drive mapping in your command.
For instance, map bulldoze Grand:\ to \\Exch-2016\c$
DISM /Online /Cleanup-Image /RestoreHealth /Source:M:\Windows\winsxs /LimitAccess
DISM – Inject Package
This process is outlined in KB 4477073.
Using the steps mentioned well-nigh, download the update from the Windows Update Catalog and then use DISM to inject the package into the running Os.
Once the package has been installed, then re-run /RestoreHealth command.
That sounds great but you may have to expand the downloaded MSU file so use DISM to inject the relevant CAB file. This could be summarised as:
-
Aggrandize the downloaded file to a binder. For example:
-
Expand.exe C:\Temp\FileWeDownloadedNameGoesHere.msu /F:* C:\Temp\Extracted
-
-
Employ DISM to inject the extracted CAB
-
DISM /Online /Add-Package /PackagePath:C:\Temp\Extracted\SomeFileName.cab
-
-
DISM /Online /Cleanup-Image /RestoreHealth
Cheers,
Rhoderick
kirbywitroubt1946.blogspot.com
Source: https://blog.rmilne.ca/2021/02/10/unable-to-install-windows-updates-or-windows-components/
0 Response to "Failed to Create Cbs Worker - Waiting for a Second and Trying Again [hresult = 0x800700c1]"
Postar um comentário